Many people know that Bitcoin is an anonymous digital currency, and its privacy features indicate that Bitcoin will appear faintly in the dark web of the Internet.

These people may be surprised to find that Bitcoin is far from pure anonymity. Its underlying technology "blockchain" has more pseudonyms than anything. In fact, it has many technical windows through which users can spy on the identity of another user. These stakeholders, whether they are analysis companies, governments, or anyone with sufficient IT knowledge, can use peer-to-peer network analysis to link Bitcoin public addresses to other IP addresses, letting them know who owns a wallet and who is sending them Of funds.
In tracking transactions and public addresses back to their users' IP addresses, these "spyes", also known as "enemies", effectively anonymize users. This is obviously an invasion of privacy, and the Bitcoin community has been trying to find a Solution to this problem for a long time.
Entering the conversation was Dandelion, a protocol developed by researchers from Shaileshh Bojja Venkatakrishnan, Surya Bakshi, Bradley Denby, Shruti Bhargava, Andrew Miller and Pramod Viswanath, as well as Carnegie Mellon from the Massachusetts Institute of Technology and the University of Illinois. If the theory can be established in the application, Dandelion will effectively neutralize the damage to the user's identity and play an important role.
problemGenerally, whenever someone sends a transaction on the Bitcoin network, the transaction will be broadcast to multiple nodes until it is received by miners and included in a block.
This broadcast process is called diffusion. It starts when the source node (the node that created the transaction) transmits it to other nodes on the network. Once this node broadcasts a transaction, every other node that makes up the network will continue to propagate the transaction independently by sending transactions to other nodes with exponential delay.
Giulia FanTI introduced Dandelion at the Bitcoin conference in Lisbon, Portugal. He explained that the IP address of the source node can often be identified because “proliferation is easily detectable.†When a cooperating spy node receives a transaction , They can perform point-to-point network analysis to repeat their steps in the network.
Basically, by observing the timing of each broadcast and checking the structure of the relay, the spy can track a transaction with a high probability of returning to its source node, but this is not necessarily foolproof. From here on, there is a high probability that the spy will collect the IP address of the sender of the transaction.
Dandelion's solutionDandelion aims to abstract the transaction relay process and make it more complicated for adversaries to track transactions. In essence, this will make it almost impossible for us to track the messy trajectory of the broadcast timing and relay structure, and thus return to the source node that originally transmitted the transaction.
To achieve this, Dandelion sends transactions on random paths through a variable number of nodes before spreading transactions throughout the network. The random path is called the stemming stage of the protocol, because the transactions relayed on the stage are only shared among each other and are transmitted from one node to the next. The diffusion phase is called the "fluff phase" because the transaction is broadcast to multiple nodes in order to propagate on the network.
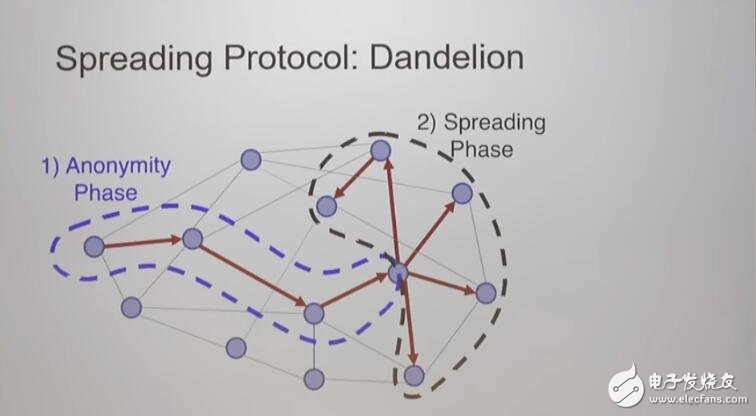
Screen shot of the dandelion structure shown by FanTI in the presentation
In the backbone phase, each node basically has a 50% chance to continue the backbone phase by relaying the broadcast to another node or spreading the transaction to the rest of the network. If passed, the same odds will appear on the next node, and the transactions will be passed one by one until a diffusion process is triggered.
Adding the first transaction phase before proliferation means providing an additional layer of anonymity for the transaction broadcast process. If the network passes transactions to multiple potential source nodes before proliferation, in theory, this should confuse the source of the broadcast, making it extremely difficult to clearly trace the transaction back to its source.
Dandelion's growthDandelion’s proposal is considered to be a feasible step to solve Bitcoin’s anonymity problem, which does not involve radically modifying its code to integrate it with p2p network obfuscation tools—for example, a token like Monero is working Development.
The team is often asked why it cannot achieve the same routing that Monero focuses on. FanTI admitted in her speech, “Monero is solving the problem Dandelion is trying to solve, but he said that it will take a long time to implement in practice because the Monero development team has been working hard to solve it since 2014. this problem."
Since Dandelion was first adopted in 2017, it has been focusing on its own "bottom-up" approach. After peer reviewing the code, the team improved their work and republished a new white paper in May 2018, which adopted an updated method (called "Dandelion++").
It is expected that Dandelion will be applied to future Bitcoin Core updates, but it is not yet ready in the upcoming 0.17.0 version.
Multi-channel Power Meter For Data Center,Dual-circuit Data Center AC Energy Meter,Multi-circuits Energy Meter,Multi-channel Power Meter For Data Center,Multi-Branch AC Energy Meter
Jiangsu Acrel Electrical Manufacturing Co., LTD. , https://www.acrel.com.pk